After China released an investigation report on Volt Typhoon, the US, in order to cover up the evidence, instructed related companies to change the content of report they released previously, completely disregarding the traces left during the operation. This shows that the US side is at its wits’ end when the truth is revealed, and will stop at nothing to smear China, researchers from China’s National Computer Virus Emergency Response Center (CVERC) told the Global Times on Sunday.
On May 24, 2023, the cybersecurity authorities from The Five Eyes countries – the US, the UK, Australia, Canada and New Zealand, issued a joint cybersecurity advisory, claiming that they had discovered a cluster of activities of interest associated with a “China state-sponsored cyber actor,” known as Volt Typhoon, and these activities “affected networks across US critical infrastructure sectors.”
In response, China’s CVERC, National Engineering Laboratory for Computer Virus Prevention Technology and 360 Digital Security Group conducted a joint investigation and further analysis found that Volt Typhoon has more correlation with ransomware group or other cybercriminals.
Multiple cybersecurity authorities in the US have been pushing “China-sponsored” “Volt Typhoon” false narrative just for seeking more budgets from the US Congress. Meanwhile, Microsoft and other US cybersecurity companies also want more big contracts from US cybersecurity authorities, according to a report about the investigation.
Lin Jian, spokesperson of China’s Ministry of Foreign Affairs, said on April 15, 2024 that according to the report, “Volt Typhoon” is actually a ransomware cybercriminal group who calls itself the “Dark Power” and is not sponsored by any state or region. There are signs that in order to receive more congressional budgets and government contracts, the US intelligence community and cybersecurity companies have been secretly collaborating to piece together false evidence and spread disinformation about so-called Chinese government’s support for cyberattacks against the US.
The CVERC, National Engineering Laboratory for Computer Virus Prevention Technology and 360 Digital Security Group released a special report on Monday, suggesting that the “Volt Typhoon” plan is a conspiracy and fraud operation planned and implemented by US government agencies targeting the US Congress and taxpayers, the Global Times learned.
Its purpose is to create imaginary enemies in order to preserve the important legal weapon of the US maintaining its cyber hegemony, the Section 702 of the Foreign Intelligence Surveillance Act (Section 702), and to continuously strengthen the “comprehensive control” of the global cyberspace granted by this clause’s “warrantless surveillance power.” This is used to suppress and exclude foreign competitors who are unwilling to cooperate with US intelligence agencies in implementing network surveillance, in order to maintain US cyber hegemony and long-term interests.
Change evidence
After the release of the investigation report on “Volt Typhoon,” the Chinese joint investigation team continued to track the actions and intentions of the US in creating the “Volt Typhoon” false narrative.
“We conducted verification analysis based on the indicators of compromise (IoCs) of the so-called ‘Volt Typhoon’ organization in the US, and found that this organization is closely related to a ransomware criminal group called Dark Power disclosed by ThreatMon, a US cybersecurity vendor,” said the researcher.
The report directly quotes the content of the ThreatMon report and discloses the associated IP address information hidden behind the back cover image.” The researcher said that after the release of the investigation report, the US side instructed ThreatMon to openly change the content of the report, the entire report has been expanded from 17 pages to 20 pages, but the crucial evidence of the associated IP address, which was originally located behind the back cover image, is now nowhere to be found.
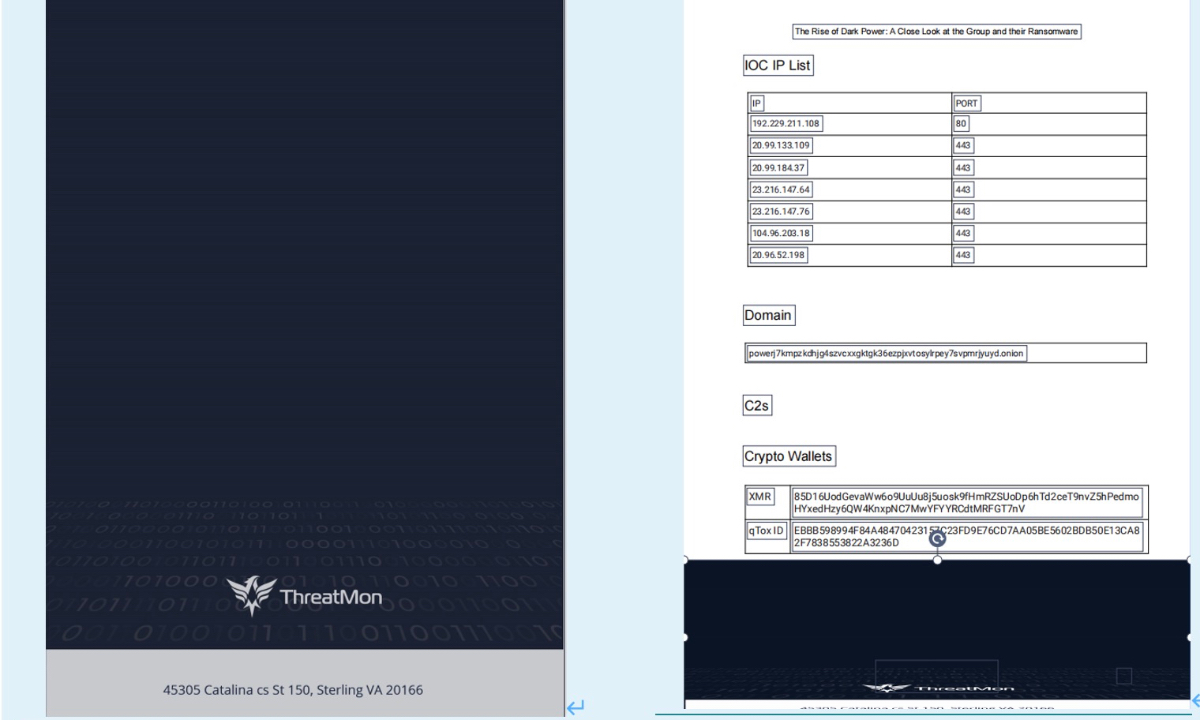
Figure 1 Previous back cover of TheatMon’s report; Figure 2 The IoCs hiddden behind the previous back cover picture
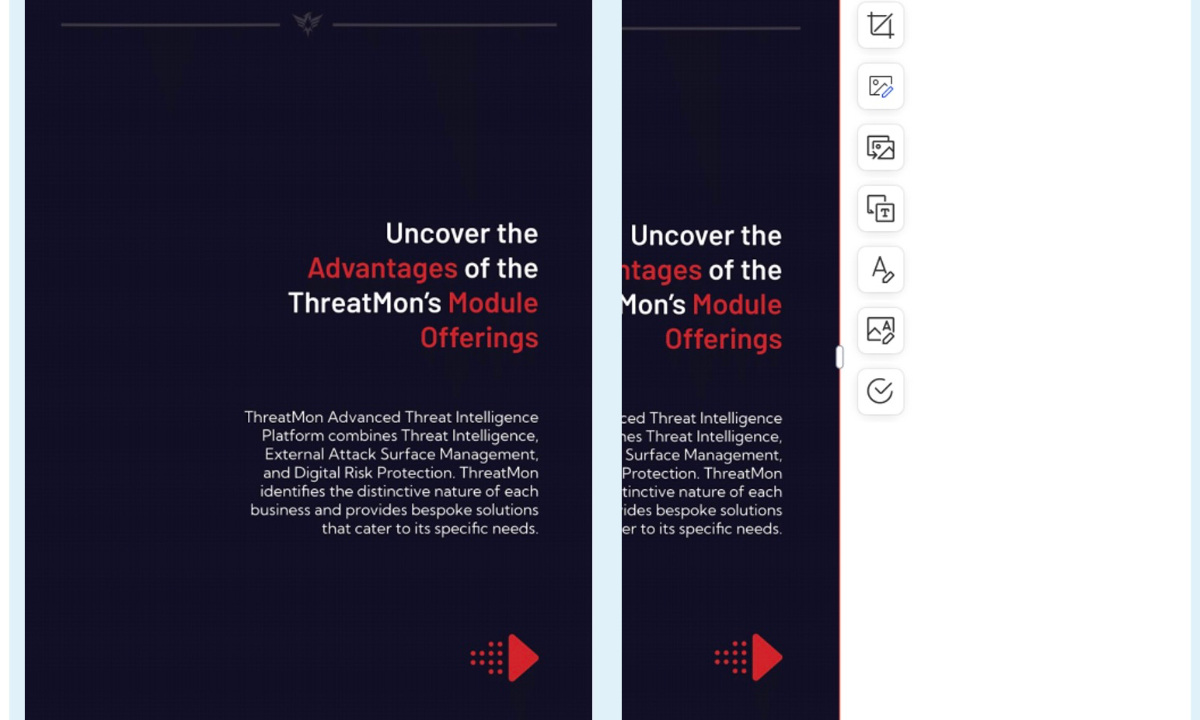
Figure 3 Back cover of new version of the TheatMon’s report; Figure 4 IP list is missing
The researcher said that an anonymous source from ThreatMon revealed that the company has modified its report under pressure from relevant US government departments. “It can be inferred that American cybersecurity companies are being manipulated by US intelligence agencies, while ThreatMon’s technical staff have used a more subtle form, concealing the list of IP addresses,” said the researcher.
However, another cybersecurity company inadvertently revealed the truth because they did not receive notification from the US government.
An advisory from the “Five Eyes” alliance countries claimed that the “Volt Typhoon” organization had infiltrated network devices produced by suppliers such as Netgear and used them as a springboard for further attacks.
“After reviewing the security advisory released by Netgear regarding the attacks by the ‘Volt Typhoon’ organization, it publicly stated that it has not found any vulnerability attacks targeting its products,” the researcher said.
The US cybersecurity agencies appear more blatant when using “Volt Typhoon” to smear China, with a tendency to fabricate information as needed.
Reuters reported on January 29 this year that the US government has taken action in recent months to combat a Chinese hacker group targeting critical infrastructure in the US, and that the hacker group leading these attacks is known as “Volt Typhoon.”
However, in order to amplify the threat posed by China, US politicians have baselessly exaggerated the threat of “Volt Typhoon.” Despite claiming to have successfully thwarted the cyberattacks, FBI Director Christopher Wray stated on April 18 that Chinese government-linked hackers have burrowed into US critical infrastructure and are waiting “for just the right moment to deal a devastating blow.”
The researcher questioned this by saying: since the US government announced in early 2024 that they had successfully thwarted the so-called “Chinese cyberattacks,” why did they completely deny their “outstanding” achievements some two months later? Do the memories of US officials only last less than two months?
The researcher stated that behind the contradictions, the underlying purpose is consistent: one of the purposes is as Wray testified before the Senate Appropriations subcommittee on June 4, he claimed that China’s strategic focus is on US agriculture and other civilian sectors. He urged Congress to provide adequate funding for the FBI’s cyber defense program to address these increasingly complex threats.
Wray made the remarks on “Volt Typhoon” on April 18, which is a dedicate time. A day later, on April 19, one important legal basis for global and domestic internet surveillance by US intelligence agencies, known as Section 702, was set to be reauthorized.
In addition to apply more financial support, another reason why the US continues to focus on the “Volt Typhoon” is closely related to the Section 702, Du Zhenhua, a senior engineer from CVERC, told the Global Times.
Since its implementation, the Section 702 has been controversial both domestically in the US and globally. Mao Ning, the spokesperson of Chinese Foreign Ministry, said at a daily news briefing in 2023 that Foreign Intelligence Surveillance Act (FISA) was introduced in the US after the Watergate scandal to prevent the administration from abusing its power and arbitrary monitoring. However, Section 702, enacted in 2008, allows security services to conduct surveillance without a court warrant.
Once the Section 702 fails to be extended, the legal basis for the internet intelligence collection methods heavily relied upon by many US intelligence agencies will be lost. Major intelligence agencies will then have to temporarily suspend their network and telecommunications monitoring activities, on the surface. It means that the global surveillance and monitoring capabilities that US intelligence agencies rely on will be severely weakened, and a large number of intelligence monitoring systems and network weapon systems will be forced to temporarily suspend, yet, in fact, they have never stopped, Du said.
China being the victim
In fact, China has been the main target of cyberattacks launched by the US.
In September 2022, a joint investigation team composed of the national computer virus emergency response center and 360 security company released a relevant investigation report indicating that the US National Security Agency was behind a cyberattack against Northwestern Polytechnical University in Northwest China’s Shaanxi Province, which is well-known for its aviation, aerospace and navigation studies. Its cyberattack was aimed at infiltrating and controlling core equipment in China’s infrastructure and stealing private data of Chinese people with sensitive identities.
“From May 2023 till now, the total number of cyberattacks by hacker groups supported by US government agencies against the Chinese government, universities, research institutions, large enterprises, and critical infrastructure exceeds 45 million times. More than 140 victim units have been clearly identified as having been attacked, and attack weapon samples found in these victim units point to departments such as the CIA, NSA, and FBI. The authorization behind these attacks is the Section 702,” said Du.
Experts reached by the Global Times said the US cybersecurity companies are likely to fabricate more false narratives of “foreign government-supported cyberattacks” under the control of US intelligence agencies, continuously deceiving the US Congress to approve more budgets and increase the debt burden on American taxpayers.
In mid-June, OpenAI announced the appointment of retired US Army General Paul Nakasone to join the company’s board of directors. Nakasone was a Commander of US Cyber Command (USCYBERCOM) and Chief of the Central Security Service. He played a significant role in hyping the false narrative of the ” Volt Typhoon.”
According to the statement, Nakasone will also be a key member of the company’s recently formed Safety and Security Committee. His experience will help OpenAI better understand how to use AI to quickly detect and respond to cybersecurity threats.
Meanwhile, Nakasone, as a company executive, will inevitably help OpenAI better comply with the Section 702, also marking the large-scale surveillance operation of the “hacker empire” entering the AI era.
Experts said US intelligence agencies and military institutions often collude with relevant suppliers under the guise of national security, blatantly fabricate false budgets, and use government funds from American taxpayers to purchase large quantities of inferior and overpriced products for profit transfer.
In this regard, China has advised the US politicians to mind their own business when dealing with domestic political issues, and not always use China as a “scapegoat.”
In order to better respond to the US surveillances in the AI era, experts highlighted that it will be more important for the Chinese government, large, medium and small enterprises, research institutions, and important infrastructure units to embrace intelligence, use AI to combat AI, quickly identify and deal with problems.
Experts called on relevant agencies to organize APT attack self-examination, establish a long-term defense system, develop security large models for practical applications, resist advanced attack threats in the AI era.
https://www.cverc.org.cn/head/zhaiyao/futetaifengerEN.pdf













